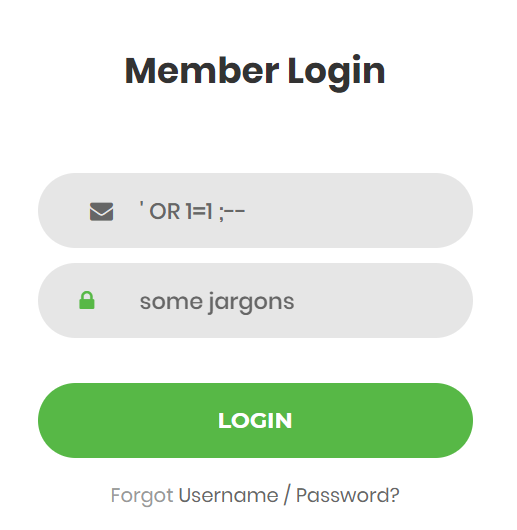
Sql Injection Hack Username Password . Here, we use the inputs: sql injection is one of the most common web hacking techniques. the simplest way to do this is to iterate over the entire password space. so you have a website with a login form, and you want to figure out how you can use sql injection to successfully. we can use sql injection to bypass the login and get access. select * from users where login='admin' and password='1' or '1'='1'; Sql injection is the placement of malicious. 1' or '1'='1 and password: This is the vulnerable application we will be trying to hack with a sql injection attack. This list contains payloads to bypass the login via xpath, ldap and sql injection (in that order). The first query type we’ll learn is the select query used to retrieve data from the database. Provided that he knew admin username.
from medium.com
we can use sql injection to bypass the login and get access. Provided that he knew admin username. Sql injection is the placement of malicious. This is the vulnerable application we will be trying to hack with a sql injection attack. sql injection is one of the most common web hacking techniques. 1' or '1'='1 and password: The first query type we’ll learn is the select query used to retrieve data from the database. the simplest way to do this is to iterate over the entire password space. so you have a website with a login form, and you want to figure out how you can use sql injection to successfully. Here, we use the inputs:
Let’s Learn SQL Injection and Bypass Login by sachith sujeewa Medium
Sql Injection Hack Username Password select * from users where login='admin' and password='1' or '1'='1'; select * from users where login='admin' and password='1' or '1'='1'; Provided that he knew admin username. The first query type we’ll learn is the select query used to retrieve data from the database. sql injection is one of the most common web hacking techniques. 1' or '1'='1 and password: Here, we use the inputs: we can use sql injection to bypass the login and get access. This list contains payloads to bypass the login via xpath, ldap and sql injection (in that order). This is the vulnerable application we will be trying to hack with a sql injection attack. Sql injection is the placement of malicious. so you have a website with a login form, and you want to figure out how you can use sql injection to successfully. the simplest way to do this is to iterate over the entire password space.
From www.slideserve.com
PPT SQL injection attack PowerPoint Presentation, free download ID Sql Injection Hack Username Password so you have a website with a login form, and you want to figure out how you can use sql injection to successfully. select * from users where login='admin' and password='1' or '1'='1'; This is the vulnerable application we will be trying to hack with a sql injection attack. the simplest way to do this is to. Sql Injection Hack Username Password.
From www.youtube.com
How to get UserName and password on any website (BurpSuite) SQL Sql Injection Hack Username Password 1' or '1'='1 and password: Sql injection is the placement of malicious. The first query type we’ll learn is the select query used to retrieve data from the database. sql injection is one of the most common web hacking techniques. select * from users where login='admin' and password='1' or '1'='1'; the simplest way to do this is. Sql Injection Hack Username Password.
From medium.com
“Defend the ” writeup (SQLi2 SQLi — Hacking admin username Sql Injection Hack Username Password Provided that he knew admin username. the simplest way to do this is to iterate over the entire password space. Sql injection is the placement of malicious. select * from users where login='admin' and password='1' or '1'='1'; The first query type we’ll learn is the select query used to retrieve data from the database. This is the vulnerable. Sql Injection Hack Username Password.
From www.sectigo.com
Understanding SQL Injection Attacks Sectigo® Official Sql Injection Hack Username Password the simplest way to do this is to iterate over the entire password space. Provided that he knew admin username. so you have a website with a login form, and you want to figure out how you can use sql injection to successfully. This is the vulnerable application we will be trying to hack with a sql injection. Sql Injection Hack Username Password.
From amandaguglieri.github.io
BurpSuite Labs SQL injection Hacking Life Sql Injection Hack Username Password Sql injection is the placement of malicious. select * from users where login='admin' and password='1' or '1'='1'; 1' or '1'='1 and password: so you have a website with a login form, and you want to figure out how you can use sql injection to successfully. sql injection is one of the most common web hacking techniques. . Sql Injection Hack Username Password.
From www.pinterest.com.mx
Tools SQL_Injection Hacking Havij Advanced SQL Injection Sql Injection Hack Username Password select * from users where login='admin' and password='1' or '1'='1'; The first query type we’ll learn is the select query used to retrieve data from the database. Sql injection is the placement of malicious. This is the vulnerable application we will be trying to hack with a sql injection attack. Provided that he knew admin username. the simplest. Sql Injection Hack Username Password.
From slideplayer.com
HandsOn Ethical Hacking and Network Defense ppt download Sql Injection Hack Username Password we can use sql injection to bypass the login and get access. sql injection is one of the most common web hacking techniques. Sql injection is the placement of malicious. The first query type we’ll learn is the select query used to retrieve data from the database. so you have a website with a login form, and. Sql Injection Hack Username Password.
From www.youtube.com
SQL Injection UNION Attack Retrieving Usernames and Passwords Final Sql Injection Hack Username Password select * from users where login='admin' and password='1' or '1'='1'; sql injection is one of the most common web hacking techniques. This list contains payloads to bypass the login via xpath, ldap and sql injection (in that order). we can use sql injection to bypass the login and get access. The first query type we’ll learn is. Sql Injection Hack Username Password.
From systemweakness.com
SQL Injection Attacks. What is a SQL Injection attack? by ADITYA Sql Injection Hack Username Password Here, we use the inputs: sql injection is one of the most common web hacking techniques. the simplest way to do this is to iterate over the entire password space. Sql injection is the placement of malicious. The first query type we’ll learn is the select query used to retrieve data from the database. Provided that he knew. Sql Injection Hack Username Password.
From medium.com
SQL Injection Hacking Attacks Medium Sql Injection Hack Username Password Here, we use the inputs: the simplest way to do this is to iterate over the entire password space. we can use sql injection to bypass the login and get access. select * from users where login='admin' and password='1' or '1'='1'; Provided that he knew admin username. 1' or '1'='1 and password: sql injection is one. Sql Injection Hack Username Password.
From www.thesslstore.com
SQL Injection Attack What It Is & How to Protect Your Business Sql Injection Hack Username Password This list contains payloads to bypass the login via xpath, ldap and sql injection (in that order). Provided that he knew admin username. select * from users where login='admin' and password='1' or '1'='1'; The first query type we’ll learn is the select query used to retrieve data from the database. so you have a website with a login. Sql Injection Hack Username Password.
From techofide.com
SQL Injection Attack (SQLi) SQL Injection Prevention Sql Injection Hack Username Password so you have a website with a login form, and you want to figure out how you can use sql injection to successfully. This is the vulnerable application we will be trying to hack with a sql injection attack. 1' or '1'='1 and password: This list contains payloads to bypass the login via xpath, ldap and sql injection (in. Sql Injection Hack Username Password.
From www.slideshare.net
SQL INJECTION EXAMPLE username Sql Injection Hack Username Password select * from users where login='admin' and password='1' or '1'='1'; Here, we use the inputs: the simplest way to do this is to iterate over the entire password space. so you have a website with a login form, and you want to figure out how you can use sql injection to successfully. Provided that he knew admin. Sql Injection Hack Username Password.
From www.youtube.com
SQL Injection Vulnerability Allowing Login Bypass Hacking the Admin Sql Injection Hack Username Password the simplest way to do this is to iterate over the entire password space. This list contains payloads to bypass the login via xpath, ldap and sql injection (in that order). The first query type we’ll learn is the select query used to retrieve data from the database. Sql injection is the placement of malicious. select * from. Sql Injection Hack Username Password.
From medium.com
“Defend the ” writeup (SQLi2 SQLi — Hacking admin username Sql Injection Hack Username Password so you have a website with a login form, and you want to figure out how you can use sql injection to successfully. Sql injection is the placement of malicious. the simplest way to do this is to iterate over the entire password space. select * from users where login='admin' and password='1' or '1'='1'; 1' or '1'='1. Sql Injection Hack Username Password.
From hackispower.blogspot.com
Hack Site’s Admin login Using Havij Sql Injection Tool Full Detailed Sql Injection Hack Username Password so you have a website with a login form, and you want to figure out how you can use sql injection to successfully. Sql injection is the placement of malicious. This list contains payloads to bypass the login via xpath, ldap and sql injection (in that order). we can use sql injection to bypass the login and get. Sql Injection Hack Username Password.
From www.youtube.com
What is SQL injection? How it Works How to Hack site Using SQL Sql Injection Hack Username Password This is the vulnerable application we will be trying to hack with a sql injection attack. The first query type we’ll learn is the select query used to retrieve data from the database. Sql injection is the placement of malicious. Provided that he knew admin username. sql injection is one of the most common web hacking techniques. so. Sql Injection Hack Username Password.
From www.youtube.com
SQL Injection Hack Explained Better WordPress Security WP Learning Sql Injection Hack Username Password we can use sql injection to bypass the login and get access. 1' or '1'='1 and password: Here, we use the inputs: The first query type we’ll learn is the select query used to retrieve data from the database. the simplest way to do this is to iterate over the entire password space. sql injection is one. Sql Injection Hack Username Password.